COMPUTER FORENSICS
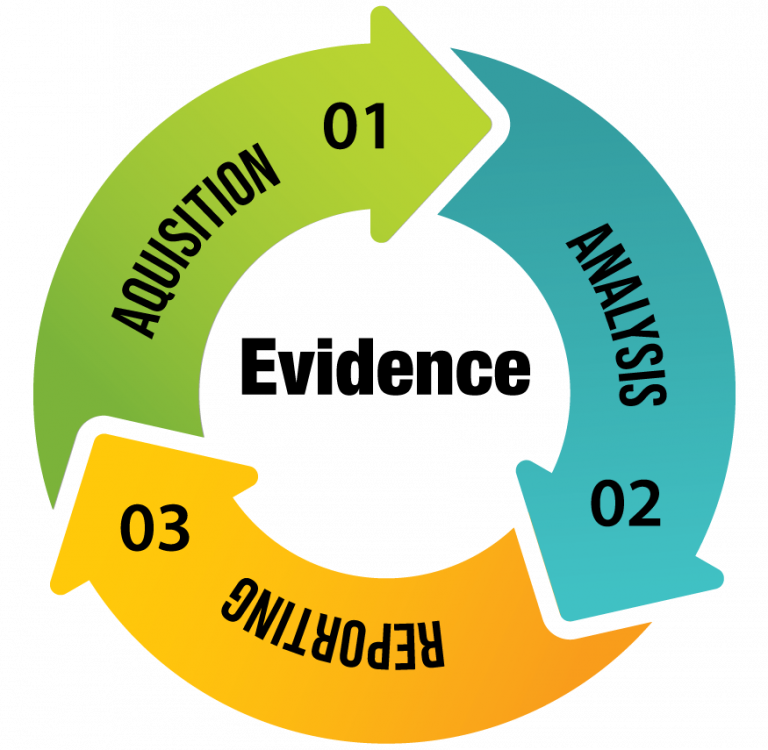
Forensic investigations are a core component of efforts to tackle a breach of security. These investigations yield results by examining data media that can provide clues about the circumstances of an incident and the culprits. Findings derived from forensic investigations by experienced independent specialists can be submitted as evidence
DIGITAL EVIDENCE RECOVERY
Evidence is collected by means of digital data. This ensures that the process is legally relevant and conducted in an appropriate manner, while providing a copy of the information for future investigation. Not only is this necessary in order to adequately analyze the incident but it will also assist with any future criminal case.
DATA RECOVERY
Loss of important information and its inaccessibility via digital media can either occur because of an accident (the result of damage, flaw, or improper usage), or a deliberate move by criminals to destroy certain data which can be used as digital evidence of a crime. The purpose of this service is to restore deleted or corrupted data stored on various media (hard drives, flash drives, and others).